Services
Secured IT system Implementation
A secured IT system refers to an information technology infrastructure that has implemented various measures and practices to protect the system's confidentiality, integrity, and availability. Here are some key elements and best practices for building a secured IT system:
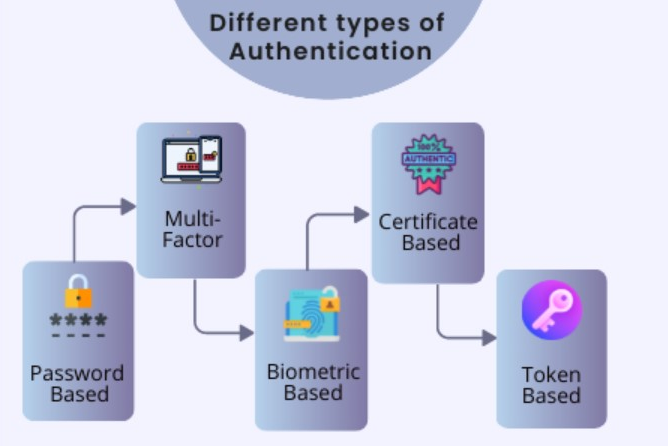
Authentication and Access Control: Implement strong user authentication mechanisms such as passwords, multi-factor authentication, or biometrics to ensure that only authorized individuals can access the system. Enforce the principle of least privilege, granting users only the minimum privileges necessary for their roles.
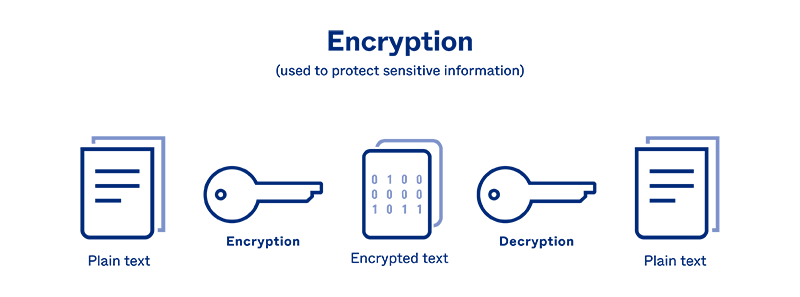
Encryption: Use encryption techniques to safeguard sensitive data both at rest (stored) and in transit (during communication). This includes employing strong encryption algorithms for data encryption, secure protocols like SSL/TLS for network traffic, and secure storage solutions for sensitive information.
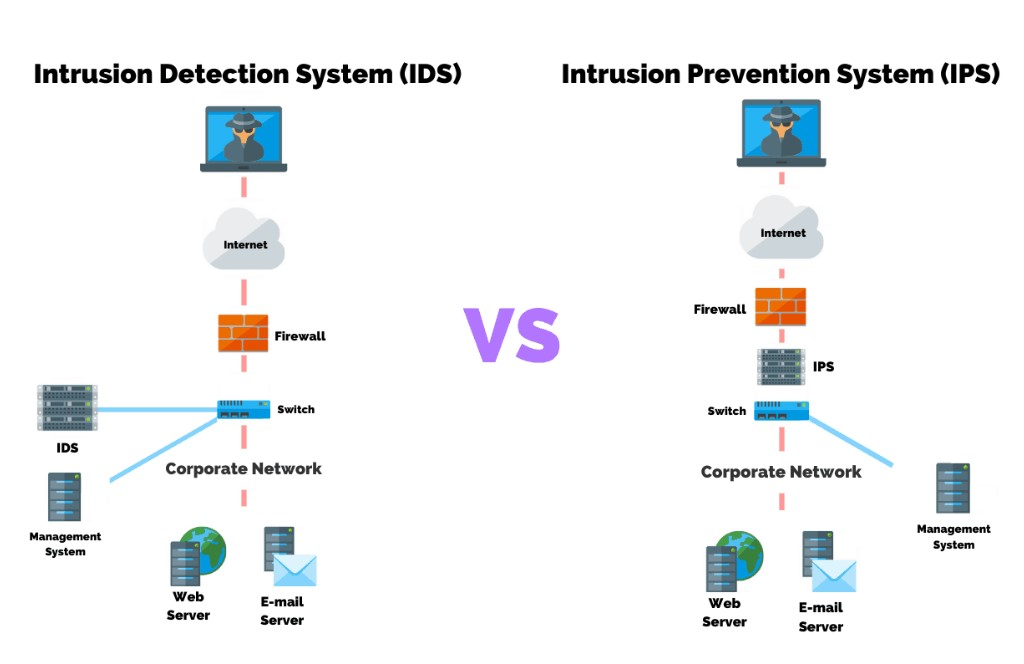
Intrusion Detection and Prevention Systems (IDS/IPS): Deploy IDS/IPS to monitor network traffic and identify any suspicious activities or potential attacks. These systems can automatically respond to threats by blocking or limiting access from suspicious sources.
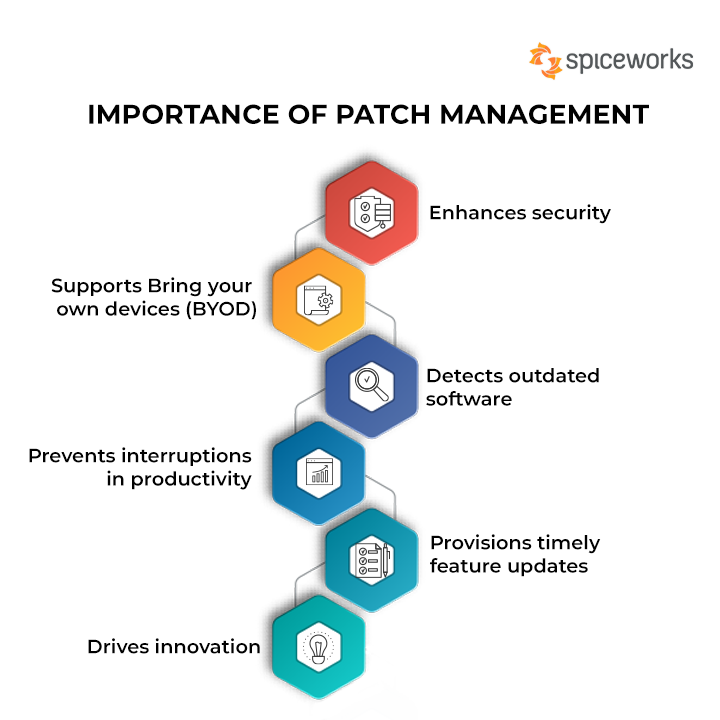
Regular Patching and Updates: Keep the operating system, applications, and all software up to date with the latest patches and security updates. Regularly apply patches to address known vulnerabilities and strengthen the overall security posture.
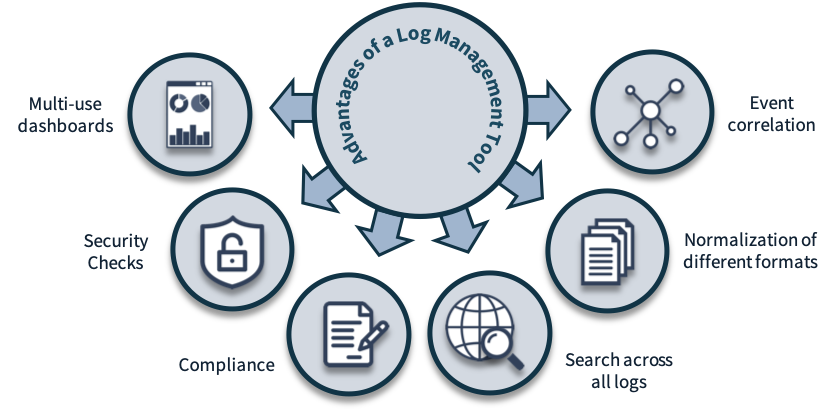
Security Monitoring and Logging: Implement robust logging mechanisms to record system activities and events. Monitor logs regularly to detect anomalies, identify security incidents, and respond promptly to any potential breaches.
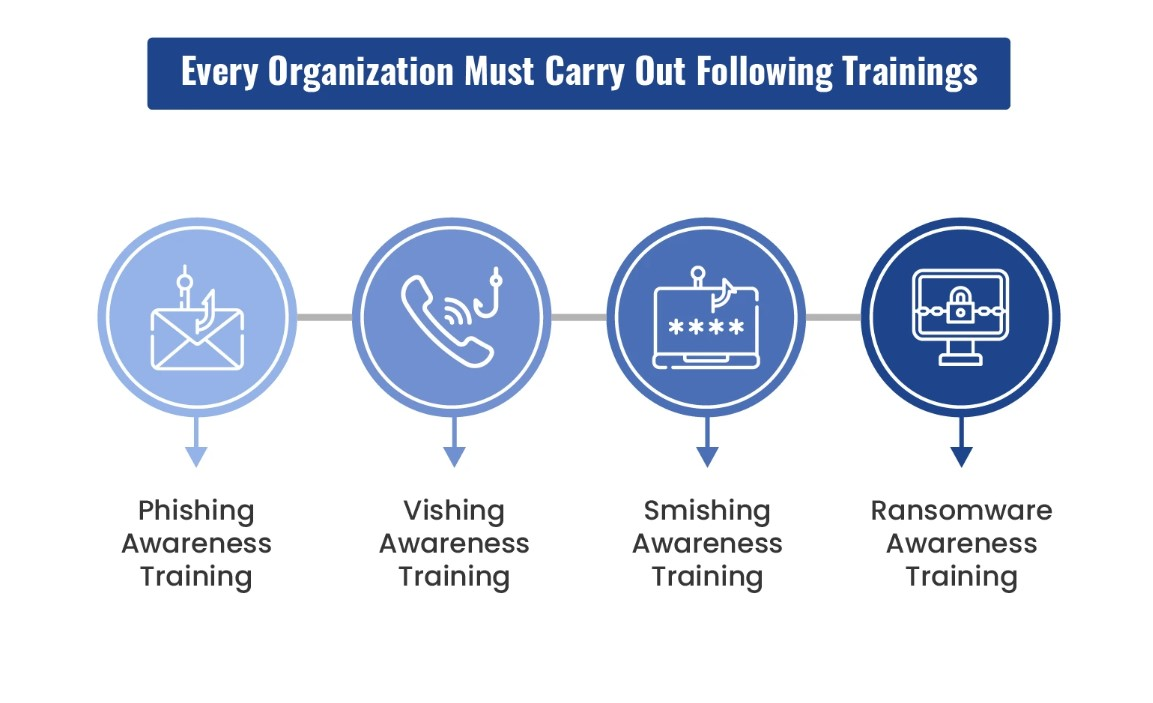
Employee Training and Awareness: Conduct regular security awareness training sessions for employees to educate them about best practices, social engineering threats, and how to handle sensitive information securely. Employees should be aware of their role in maintaining a secure IT system.
Incident Response and Disaster Recovery: Develop an incident response plan to handle security incidents effectively, including steps for containment, eradication, and recovery. Additionally, implement a disaster recovery plan to ensure business continuity in case of a major security breach or system failure.

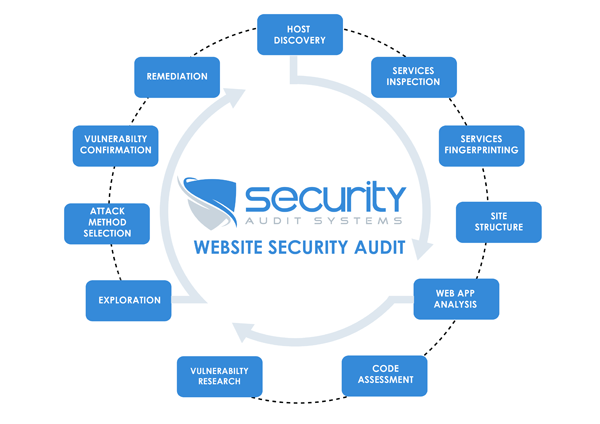
Regular Security Audits and Penetration Testing: Perform periodic security audits and penetration tests to identify vulnerabilities and weaknesses in the system. This helps in proactively addressing potential risks before they can be exploited by attackers.
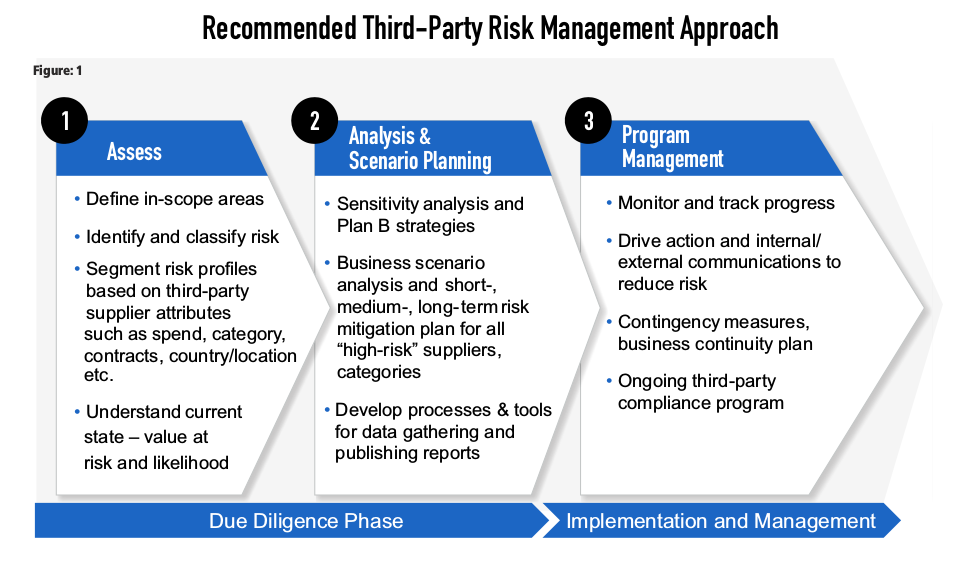
Vendor and Third-Party Risk Management: Evaluate the security practices of vendors and third-party service providers to ensure they meet your organization's security requirements. Maintain strong contracts that clearly define security obligations and responsibilities.
Remember, building a secured IT system is an ongoing process. It requires a combination of technical measures, organizational policies, and user awareness to ensure the system remains resilient against evolving threats.
Implementing a secure IT system involves a series of steps and considerations. Here's a high-level overview of the process:
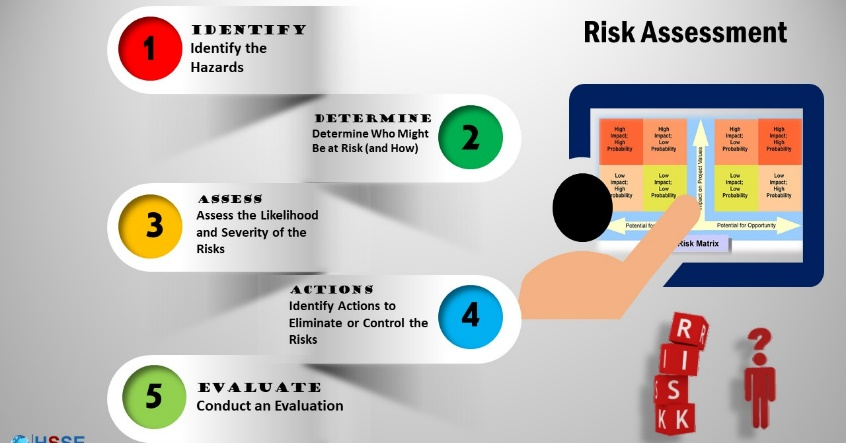
Risk Assessment: Begin by conducting a comprehensive risk assessment to identify potential vulnerabilities and threats specific to your organization's IT environment. This assessment helps prioritize security measures based on the potential impact and likelihood of risks.
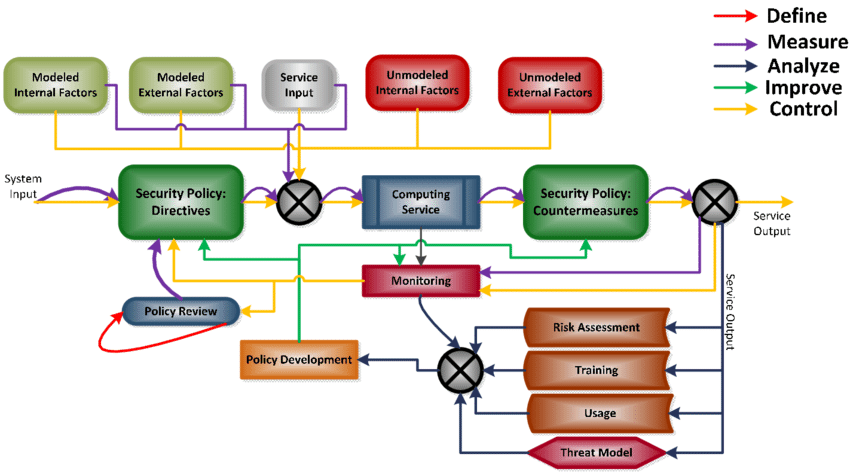
Security Policy Development: Develop a set of clear and comprehensive security policies that outline the organization's security objectives, acceptable use of IT resources, password management, incident response procedures, and other relevant guidelines. Ensure these policies align with industry best practices and legal/regulatory requirements.
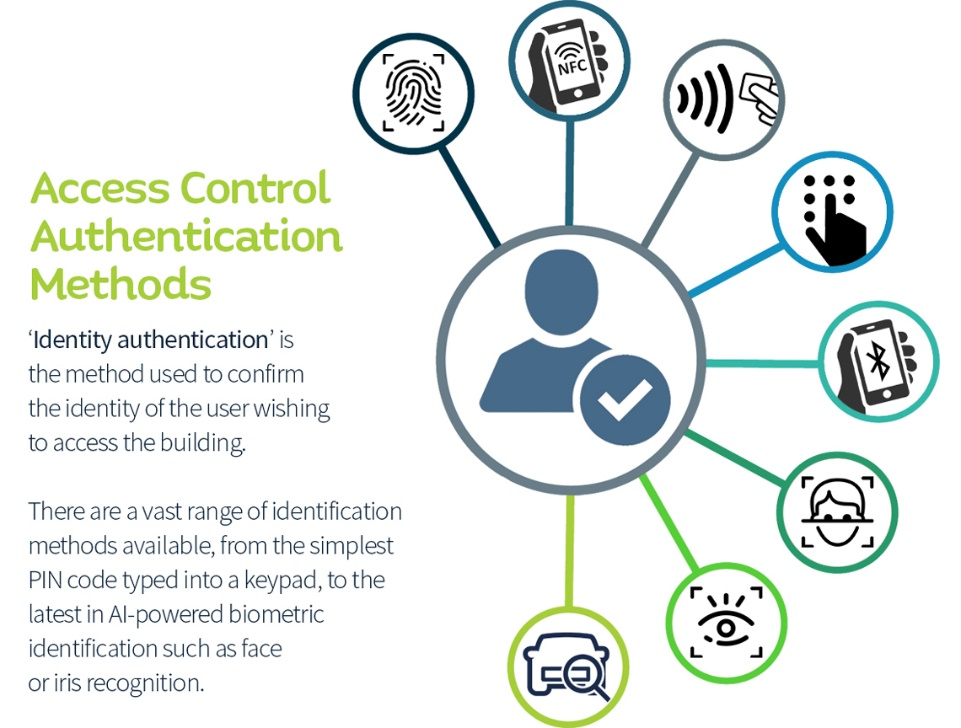
Access Control and Authentication: Implement strong authentication mechanisms such as passwords, biometrics, or multi-factor authentication (MFA) to verify user identities. Enforce the principle of least privilege, granting users only the necessary access rights for their roles.
Network Security: Deploy firewalls, intrusion detection/prevention systems (IDS/IPS), and virtual private networks (VPNs) to protect your network perimeter. Segment your network to isolate critical systems and data from potential threats. Regularly monitor network traffic and update security configurations as needed.
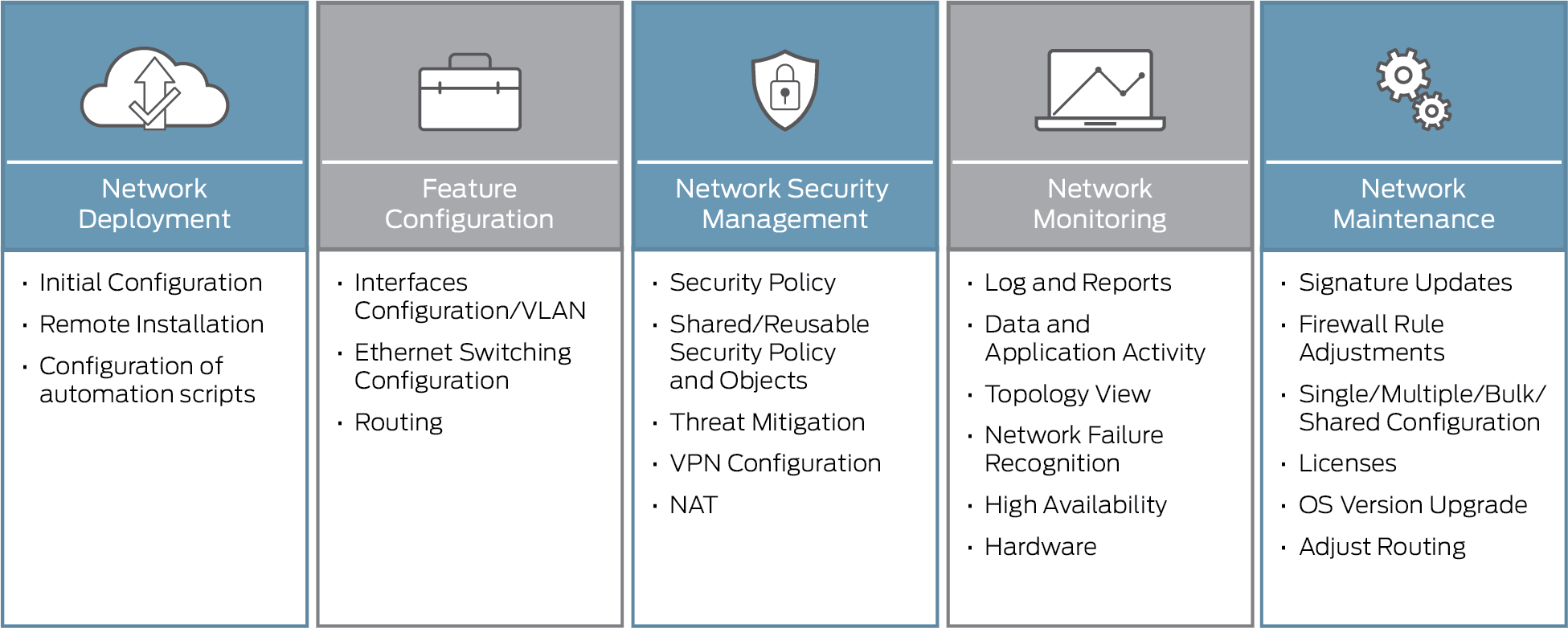
Secure Configuration: Follow industry best practices and harden the configuration of your IT systems and infrastructure components. Disable unnecessary services, change default passwords, and apply security patches and updates promptly.
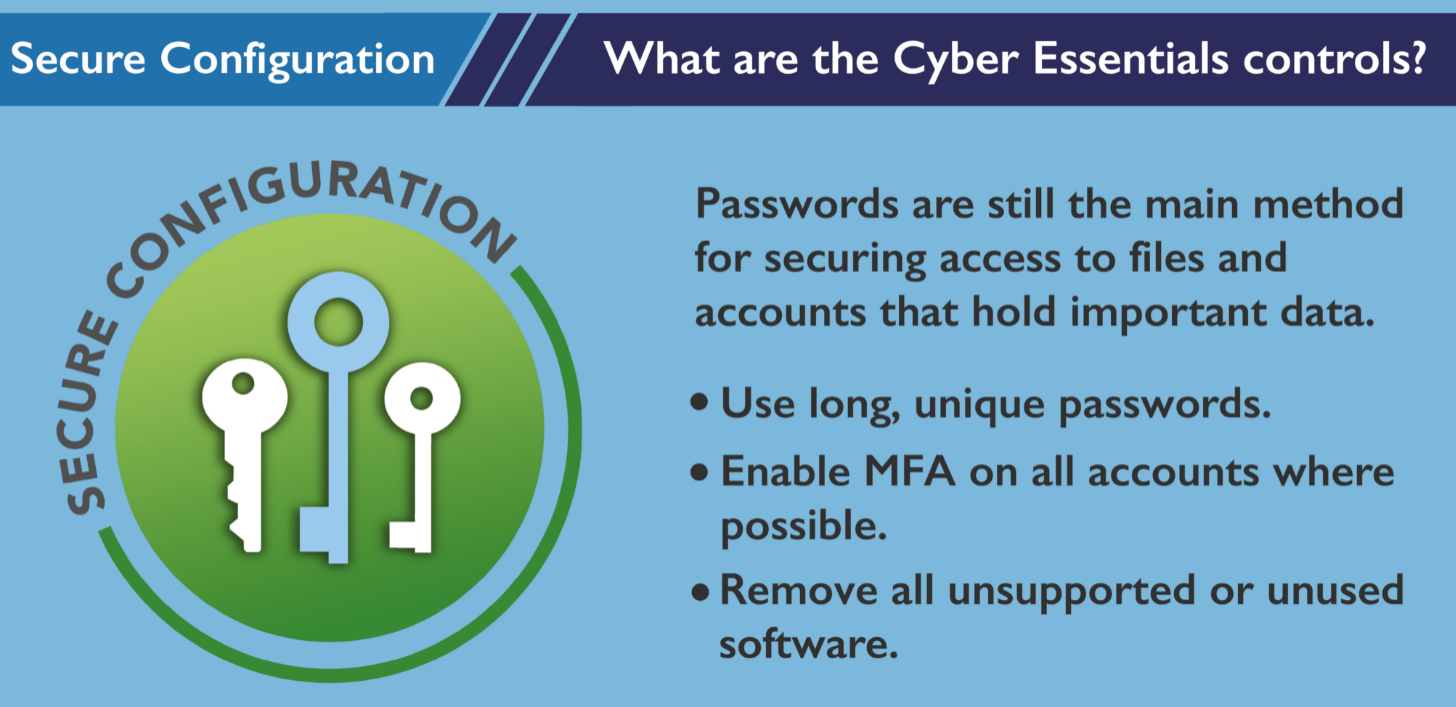
Data Protection: Implement encryption techniques to protect sensitive data both at rest and in transit. Utilize encryption algorithms and secure protocols for data storage, data transfer, and communication. Consider data loss prevention (DLP) solutions to prevent data leakage.
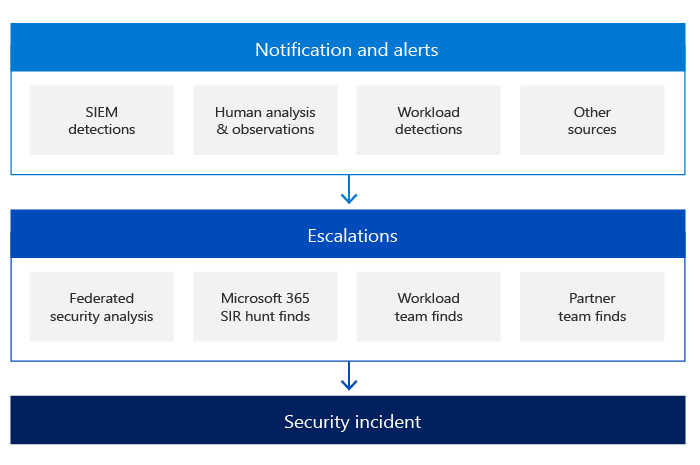
Security Monitoring and Incident Response: Deploy security monitoring tools to detect and respond to security incidents. Set up log management systems to collect and analyze system logs. Establish an incident response plan to effectively handle security incidents, including containment, investigation, eradication, and recovery steps.
Regular Assessments and Updates: Perform regular security assessments, penetration testing, and vulnerability scanning to identify and address any new or emerging security risks. Stay updated with security news, advisories, and patches from vendors and security communities.
Continual Improvement: Maintain an ongoing commitment to security by regularly reviewing and updating your security controls, policies, and procedures. Stay informed about evolving threats and emerging technologies to adapt your security measures accordingly.
Remember, the implementation of a secure IT system requires a multi-layered approach, involving both technical and organizational measures. It's important to adapt these guidelines to your organization's specific needs and regularly reassess and improve your security practices to stay ahead of potential threats.
