Services
Approaches to Information Security Implementation
Information security, or infosec, refers to data security — one component of a larger cybersecurity plan that takes proactive steps to protect data. Key areas of an infosec program include controlling who can access what data, what level of access each authorized person is given, employee training, and accommodations for your specific data needs.
An infosec program is necessary for any company responsible for managing personal or client data, including healthcare facilities, financial institutions, utility businesses, property managers, and schools. In some countries and industries, data protection is legally required.
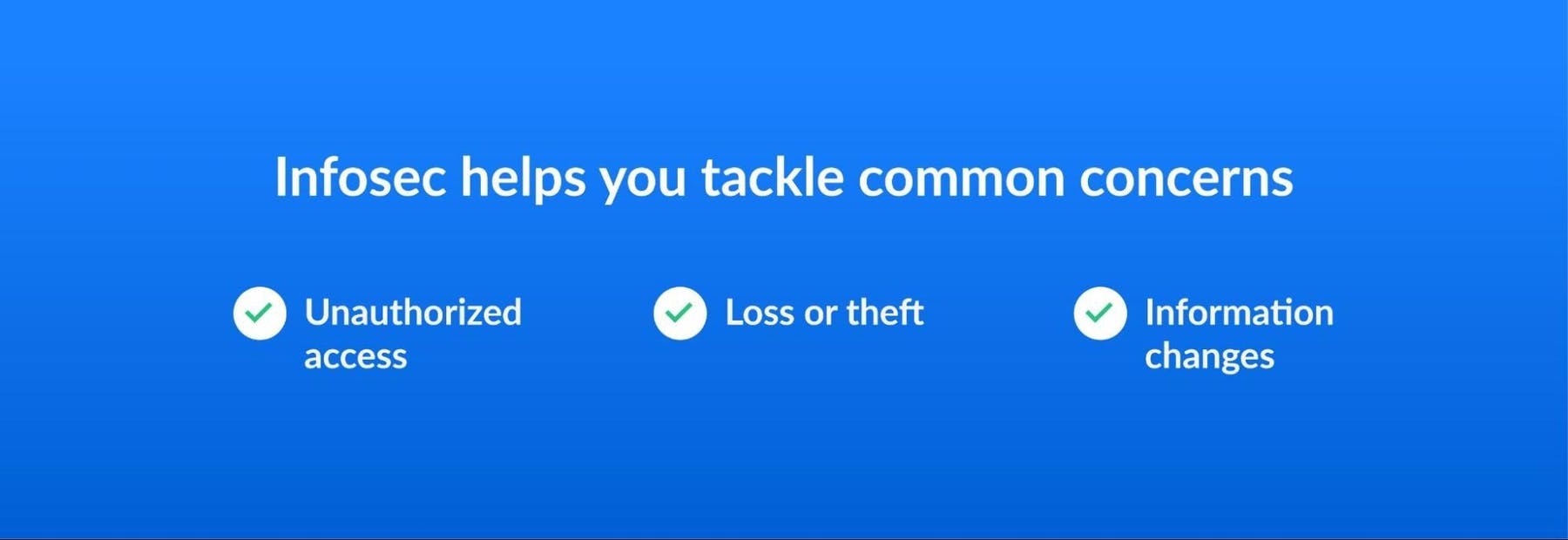
Infosec will help you keep data safe from :
- Unauthorized access : Data breaches are a top concern across industries, costing an average of nearly $4 million and causing 60% of small businesses to close after their inability to recover
- Loss or theft : Information security protects against unexpected disasters such as weather-related events, fire, and theft that may result in costly data loss
- Information changes : A thorough information security program ensures data remains in its original, unaltered state and is not accidentally or maliciously altered
Two popular approaches to implementing information security are the bottom-up and top-down approaches. We'll explain the difference between these two methods and provide helpful tips for establishing your own data protection plan.
1. The bottom-up approach
The bottom-up approach places the responsibility of successful information security on a single staff member or security department, such as a network security professional, on-staff cyber engineer, or other expert who doesn't hold a top-level management position. This person's primary responsibility within your company is to protect organization-wide data using their education, training, experience, and expertise.
Advantage of bottom-up implementation
The main advantage of a bottom-up approach to infosec is that you're using a person or team's experience and expertise to handle intricate security concerns. They possess all the training and industry insight needed to account for your company's unique situation.
In many cases, you may be able to assign the task to an existing employee with the appropriate background instead of hiring someone new. This is a great way to use the valuable resources already available to you and save the time or costs of securing a larger, more complex plan.
What to consider
The largest disadvantage — and the reason many industry experts recommend avoiding this approach — is that it doesn't involve assistance or input from top-level management. Because of this, your infosec program won't have the same longevity or thoroughness that it would have if you were incorporating information and directives from the top.
When you involve all your company's upper management, they have a unique vantage point of company-wide concerns, standards, requirements, and available resources.
2. The top-down approach
The top-down approach starts with upper management. Top-level managers are the ones responsible for initiating, creating, and implementing your data protection strategy, including policy creation, procedural instructions, and escalation plans. They may seek outside assistance, training, or a working partnership with a professional infosec service. They can also utilize existing staff expertise and company resources.
Advantages of top-down implementation
This approach looks at each department's data and explores how it's connected to find vulnerabilities. Managers have the authority to issue company-wide instructions while still allowing each person to play an integral part in keeping data safe. Compared to an individual or department, a management-based approach incorporates more available resources and a clearer overview of the company's assets and concerns.
A top-down approach generally has more lasting power and efficacy than a bottom-up approach because it makes data protection a company-wide priority instead of placing all the responsibility on one person or team. Data vulnerabilities exist in all offices and departments, and each situation is unique. The only way for an information security program to work is by getting every manager, branch, department, and employee in agreement with a company-wide plan.
What to consider
A successful top-down approach requires good leaders who are committed to prioritizing information security. Since existing management doesn't likely have the necessary training or experience to create an effective data protection plan, you will need to consult an outside expert.
You must ensure management has enough time and resources to implement, monitor, and maintain new policies while creating an infosec plan. The best type of top-down approach typically starts with upper management and utilizes existing IT employees to create a well-rounded program.
Implementing a layered information security
Cybersecurity is critical for businesses of all types and sizes. In one survey, more than half of participants cited cybersecurity as a top concern for their organization. Data and network compromise can have devastating effects that many businesses never fully recover from. In 2019, cyberattacks cost individual businesses an average of $200,000.
Attacks come in several forms, such as phishing scams, hacking, unauthorized access at physical locations, Trojan viruses, ransomware, and password attacks. Because there are so many possible vulnerabilities, a layered approach is the best method for implementing total protection across departments.
Infosec layering accounts for all standard data protection along with other facets of cybersecurity, including web, network, device, application, software, and physical security. It also includes having a disaster recovery and data backup plan. Layered protection breaks larger security concerns into smaller, more manageable pieces. It lets you customize the type and protection level depending on specific needs, such as department, device, or stored data.
Consider a healthcare business. In the financial department, data integrity is likely the top concern to prevent overcharging or undercharging accounts. But the patient records department focuses on data security, privacy, and access control. This is where a layered approach comes in. Layered approaches are woven together so each area of information security relies on the other, creating a stronger, more defensive blanket of protection that makes it harder for outside attackers to gain entry.
Web and network security
Web and network security cover creating policies and safeguarding all browsers, private networks, shared networks, and online user accounts, such as:
- Clearly assigned user roles for each person with access, including management, employees, third-party contractors, and partners
- Various encryption methods for on-site and off-site employees and contractors
- IP network-wide security for all network traffic
- Firewalls, antivirus and antimalware systems, intrusion alerts, and defense software
- Disabling web browser pop-ups
- Security for all webmail, including attachments and possible phishing scams
- Using a secure, up-to-date web browser with an individual, controlled employee access account
- Mobile device security for company phones, tablets, and smart devices
- Network segmentation whenever applicable
- Data loss prevention (DLP) for files and messages
Physical security
Physical security varies depending on the industry, business model, and physical premises. It includes large-scale implementations, for instance requiring access codes for data centers, as well as smaller actions, such as locking rooms with sensitive information at small businesses.

Additional physical security methods include:
- Having policies for who can access what company equipment and devices, as well as strict regulation for how they are used and where they are taken
- Installing alarm systems on doors and windows, especially for businesses who store most data on-site
- Conducting background tests and reference checks for all new hires, third-party contractors, or partners who work closely with sensitive information
- Investing in key cards, employee identification, and other controlled methods for entry to secure areas of your business
Backup and disaster recovery
Data backup and disaster recovery are an essential part of all layered security programs, no matter what size or type of business you're in. All industries are susceptible to unexpected risks, such as hurricanes, fires, floods, tornadoes, theft, global disasters, and other incidents that render your physical location inaccessible. Without a recovery and backup plan, you risk losing data, time, and profit from being temporarily out of business.

Here are some tips for backup and recovery :
Choose automatic backup
Not all backup methods can operate automatically. For instance, data sometimes must be manually backed up onto a physical device. Putting applicable devices and systems on an automatic backup schedule helps you avoid forgetting or duplicating the process. It's up to your organization's needs how often you save your data — typically daily, weekly, or monthly.
Save data in multiple locations
Ultimately, your content is more secure in the cloud. Having your critical data in the Content Cloud alleviates the physical and geographical burden of on-premises data storage and shifts the responsibility to the vendor. For-on premises data, take a layered approach to information security. Avoid storing all your company or department data in a single place, especially if it's a physical location. Some companies solve this problem by replicating and spreading data to different servers, storage devices, and a combination of on-site and off-site methods — a hybrid approach. Other businesses use options such as magnetic storage tape, local area networks (LANs), and USB drives to protect onsite data.
Enhance on-site storage protection
Any on-site storage you rely upon should be protected in a secure area free from unauthorized access. Implement locks, alarms, and ongoing monitoring if necessary. You might also invest in fireproof or water-resistant storage receptacles for portable drives and files, especially if you live in a wildfire-prone or hurricane-prone area.
Have an access plan
Businesses become inaccessible for various reasons, and no industry is exempt from the risk of natural disaster, a pandemic, or serious accidents that can shut operations down for a day or more. Should something like this happen, you will need an established plan of action for accessing on-site data and continuing daily operations to avoid costly delays. Ensure all employees are trained and aware of their roles in such situations and invest in remote equipment for distributed operations if necessary.
Implement information security programs
1. Evaluate your current situation
Consider these questions:
- What financial, IT expertise, storage hardware, cloud account, or other resources does your team currently have?
- What is your system currently capable of in terms of storage, backup, and security?
- What are your most significant security risks?
- Where are your current vulnerabilities and liabilities, and what can you improve?
If you're not sure how to answer these questions or lack the information to do so, consider scheduling a professional security audit to identify weaknesses.
2. Set goals and objectives

Where do you want your company's information security program to be in one month? How about one year or five years? Some processes, such as changing passwords, investing in better antivirus programs, and securing additional data backup options, are instantaneous. Other parts of your infosec program, such as achieving specific percentages of blocked attacks or moving large amounts of data to new systems, will take much longer.
Create a list of short-term and long-term information security goals and break them into smaller tasks that you can assign to individuals, management, and departments. You'll also want to create a method for measuring the success of those goals by creating benchmarks — for instance, a decrease in the number of reported threats each month or getting a specific security certification.
3. Identify needs and make a plan
Once you know what your situation is and where you want your company to be in the future, it's time to make a plan. Work with other members of your team and outside experts to gauge what you need to carry out your information security program and their approximate cost, such as:
- Physical storage hardware
- Cloud content management platforms
- Off-site storage facility usage
- Professional consultations and outside training from IT experts
- Supplemental staff training costs
- New security software or subscriptions
- Hardware and account upgrades
- Ongoing monitoring and maintenance
- Equipment for a distributed workforce or backup access
The people, departments, and outside professionals you involve in this plan depend on your chosen security approach. You'll generally want to include at least members of your existing IT team, an outside auditing agency, and all relevant employees.
4. Work toward compliance with optional certification
Consider working toward compliance with an optional certification program, such as the ISO/IEC 27001 standards. These standards are not mandatory in most industries, but they provide a framework for optimal information security to act as a standard for your infosec plan.
Though ISO 27001 is not the only type of compliance certification, it includes helpful guidance for topics such as:
- Audit scope and guidelines
- Types of attacks
- Industry definitions
- Risk assessments and treatment methods
- Access control policies
- Communications and operations security
- Guidelines for supplier relationships
- Human resource security
- Asset inventory, acceptable use, and management
- Incident procedures for management
5. Implement ongoing monitoring, maintenance, and updates

Infosec and layered cybersecurity programs are not leave-it-and-forget-it. They should be viewed as a living, evolving component of your company. Implement ongoing employee training to address new and trending security threats or new preventive measures. Monitor all infosec statuses and successes and make investments and protocol adjustments as needed. Keep cybersecurity plans up to date with technology and staff changes.
You should also conduct regular vulnerability assessments to identify potential new weak areas and test the effectiveness of all security measures. Annual internal audits are a great option for keeping everything and everyone operating on the same page.
